October 2022, Vol. 249, No. 10
Features
Pipeline Cybersecurity Implementation Plan for TSA Security Directive
By Marco Ayala, Director of Industrial Control Systems, 1898 & Co., a part of Burns & McDonnell
(P&GJ) — The pipeline industry has been placing focus and efforts on cybersecurity ever since last year’s Transportation Security Administration’s (TSA’s) security directives were first issued. The security directives (SDs) were a pushed rollout that caught many off-guard at the time—they knew it was coming but did not know the exact details.
It applies to owner/operators of hazardous liquid and natural gas pipelines or liquefied natural gas facilities that have been notified by TSA that their pipeline system or facility is critical.
The first SD-01, “Security Directive Pipeline-2021-01,” went into effect on May 28, 2021, with the intention of enhancing pipeline cybersecurity. It called out the following three critical functions:
- TSA-specified owner/operators must report cybersecurity incidents to the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA).
- Owner/operators must designate a cybersecurity coordinator who must be available to TSA and CISA 24/7 to coordinate cybersecurity practices and address any incidents that arise (and at least one alternate cybersecurity coordinator at the corporate level).
- Owner/operators must review their current activities against TSA’s recommendations for pipeline cybersecurity to assess cyber risks, identify any gaps, develop remediation measures and report the results to TSA and CISA.
The SD-01 also provided pipeline owner/operators TSA’s definitions for informational technology (IT) and operational technology (OT) systems, defining “disruption” and “incident.”
The second SD-02, “Security Directive Pipeline-2021-02,” went into effect July 26, 2021, defining mitigation actions, contingency planning and testing. The SD-02 is protected by Sensitive Security Information (SSI) and it calls out three elements in general.
- Implement critically important mitigation measures to reduce the risk of compromise from a cyberattack.
- Develop a Cybersecurity Contingency/Response Plan to reduce the risk of operational disruption or significant business or functional degradation of necessary capacity, as defined in this SD, should the IT and/or OT systems of a gas or liquid pipeline be affected by a cybersecurity incident.
- Test the effectiveness of the owner/operator’s cybersecurity practices through an annual cybersecurity architecture design review.
The reality is that SD-02 is very prescriptive, and industry met TSA with heavy feedback and concerns both directly and through industry associations. So much so that industry organizations banded together in their feedback to TSA. Pipeline trade associations American Fuel & Petrochemical Manufacturers (AFPM), American Gas Association (AGA), Association of Oil Pipelines (AOPL), American Petroleum Institute (API), American Public Gas Association (APGA), the Interstate Natural Gas Association of America (INGAA), and GPA Midstream together sent a letter to the TSA administrator sharing all the same concerns with implementing the directive and not arguing the concern of ransomware and other cyber threats.
The issue of unanswered technical questions submitted to TSA left operators uncertain about what is required for compliance. The key challenges were not just in timelines and the elements of the technology say provisioned running pipeline systems and potentially having limiting security capabilities or capable but with legitimate deployment concerns, but with unclear elements or defining of items such as “nonoperational networks” for example.
In the industry’s association letter to TSA:
“Operational reliability and safety are extremely important to the pipeline industry. The Directive’s potential to cause operational disruptions or threaten safe operations remains a concern of affected pipeline operators. Our pipeline operators have expert knowledge regarding their assets, how they are managed to meet customer needs, and how to comply with the various state and federal regulations under which they are required to operate.
As the Directive was developed, industry conveyed highly probable operational safety and reliability concerns that could arise by imposing prescriptive cyber requirements and untenable timelines without specific understanding of a company’s existing cybersecurity protections and operations.”
“We also urge TSA to reconsider its process for implementing pipeline security initiatives in the future to ensure better input on the compatibility of proposed security requirements with pipeline operational technology. It is important TSA make timely updates to its pipeline security policies to keep up with evolving threats. At the same time, it is equally important TSA’s process does not sacrifice input from the regulated industry for the sake of speed.”
The addendum to SD-02 “Security Directive Pipeline-2021-02B” went into effect December 17, 2021, defining mitigation actions, contingency planning, and testing. SD-02B was protected by SSI - Sensitive Security Information also calls out the same three elements as the original SD-02.
However, on June 6, the TSA issued a memorandum stating that they “made a determination that the Security Directive, SD Pipeline-2021-02B, is no longer considered to contain Sensitive Security Information (SSI) and the markings denoting the document as SSI have been removed from the attached copy of the Security Directive.”
The SD-02B provided prescriptive controls that again did have the same concerns as the original, but with cyber as a moving target anything pointing our bow in the right direction is still a positive move. The implementation timelines provided by TSA were still tight, effectively extending the operational technology (OT) sections to January 22, 2022, and assessments by July 26.
An example from the SD-02B Conduct Operational Technology System Cybersecurity Architecture Design Reviews:
“No later than January 22, 2022, unless otherwise directed, Owner/Operators must schedule a third-party evaluation of the Owner/Operator’s Operational Technology system design and architecture, to be conducted no later than July 26, 2022, which includes verification and validation of network traffic and system log review analysis to identify cybersecurity vulnerabilities related to network design,
configuration, and inter-connectivity to internal and external systems.
This evaluation must:
- Be conducted by an independent third-party, unless otherwise approved by TSA that has demonstrated capability to perform the cybersecurity architecture design review required by this Security Directive
- Be completed annually thereafter for the duration of this Security Directive, as
revised and renewed
- Include a written report detailing the results of the evaluation and the acceptance or rejection of any recommendations provided by the evaluator to address vulnerabilities. This written report must be made available to TSA upon request and retained for no less than two (2) years from the date of completion.
The SD-02C “Security Directive Pipeline-2021-02” went into effect July 27, again reinstituting mitigation actions, contingency planning, and testing and expires July 27, 2023.
SD-02C is a continuation of the SD-02 series and supersedes and replaces SD Pipeline-2021-02B and is not an SSI document.
The requirements are:
- Establish and implement a TSA-approved Cybersecurity Implementation Plan.
- Develop and maintain a Cybersecurity Incident Response Plan to reduce the risk of operational disruption.
- Establish a Cybersecurity Assessment Program and submit an annual plan that describes how the owner/operator will assess the effectiveness of cybersecurity measures.
Owner/operators must continue to implement the specific measures from Security Directive Pipeline 2021-02B, as identified in the Attachment to SD02C, and to be modified by any TSAapproved alternative measures and/or action plans, until a Cybersecurity Implementation Plan issued pursuant to this Directive is approved by TSA.
The goal of this SD is to reduce the risk that cybersecurity threats pose to critical pipeline systems and facilities by implementing layered cybersecurity measures that demonstrate a defense-in-depth approach against such threats. Recent and evolving intelligence emphasizes the growing sophistication of nefarious persons, organizations and governments; highlights vulnerabilities; and intensifies the urgency of implementing and sustaining the requirements.
The good news is that TSA did listen to the pipeline industry in its effort on cybersecurity requirements and inspections. The better part of the news and directive is that TSA is focusing more on a results-based approach than a prescriptive stance. TSA uses the terms “result”- and “performance”-based approach in different commentary and documents but have allowed for alternative measures (AM).
“This revised security directive follows significant collaboration between TSA and the oil and natural gas pipeline industry. The directive establishes a new model that accommodates variance in systems and operations to meet our security requirements,” said TSA Administrator David Pekoske. “We recognize that every company is different, and we have developed an approach that accommodates that fact, supported by continuous monitoring and auditing to assess achievement of the needed cybersecurity outcomes.”
The reissued security directive takes an innovative, performance-based approach to enhancing security, allowing industry to leverage new technologies and be more adaptive to changing environments. The security directive requires that TSA-specified owners and operators of pipeline and liquefied natural gas facilities take action to prevent disruption and degradation to their infrastructure to achieve the following security outcomes:
- Develop network segmentation policies and controls to ensure that the OT system can continue to safely operate if an IT system has been compromised and vice versa.
- Create access control measures to secure and prevent unauthorized access to critical cyber systems.
- Build continuous monitoring and detection policies and procedures to detect cybersecurity threats and correct anomalies that affect critical cyber system operations.
- Reduce the risk of exploitation of unpatched systems through the application of security patches and updates for operating systems, applications, drivers and firmware on critical cyber systems in a timely manner using a risk-based methodology.
Pipeline owners/operators are also required to:
- Develop and maintain a Cybersecurity Incident Response Plan to reduce the risk of operational disruption, or the risk of other significant impacts on necessary capacity should a cybersecurity incident affect their IT or OT systems. (Note that the attack on the Colonial Pipeline system targeted its billing functionality.)
Establish a Cybersecurity Assessment Program and submit to the TSA an annual plan that describes how the owner/operator will proactively and regularly assess the effectiveness of its cybersecurity measures and identify and resolve device, network and/or system vulnerabilities.
Technology that provides both enabling and supporting functions at the enterprise level but also real-time systems that safely and reliably operate our pipeline systems and safeguard compounding aspects of health, safety, and environment (HSE) must always take precedence.
TSA has developed and provided to owner/operators 34 new “Frequently Asked Questions (FAQs)” in August this year that help industry further clarify points on the security directives. It has, for example, compare and contrast questions and answers to specific technical questions from stakeholders like patching, firmware and backups, for example.
The sections cover general, protection of information, cybersecurity implementation plan, monitoring and detection policies and procedures, security patch and updates, cybersecurity incident response plan, cybersecurity assessment program, records, amendments to cybersecurity implementation plan and compliance.
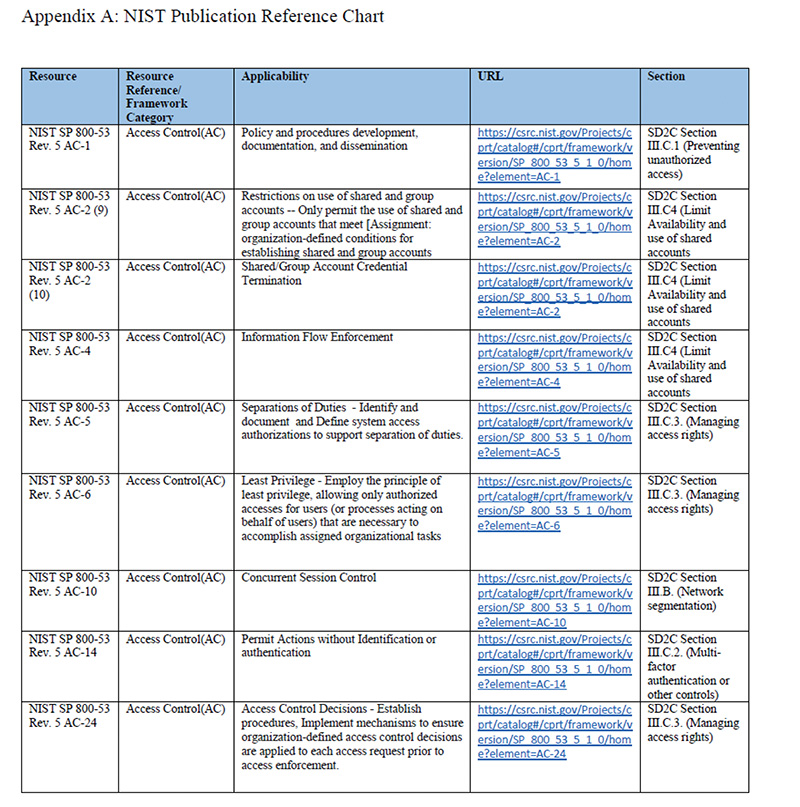
On Sept. 2, TSA just issued the “Information Supplement for the TSA Security Directive Pipeline-2021-02C, Version 1.0.” This document provides owner/operators a deeper informative document that focuses on the Cybersecurity Implementation Plan (CIP). TSA also created a generic template that owner/operators can use as added help and an appendix that outlines what should be in the owner/operators’ CIP.
The biggest help and lift from the TSA are the addition of a mapping table from National Institute of Standards and Technology’s (NIST) Cyber Security Framework (CSF) to SD-02C.
While the latest SD-02C allows owner/operators the choice of third-party assessments, TSA generally recommends it. It is strongly recommended that you consider having peer assessments and reviews with subject matter experts outside of the integrator and systems vendor because biases can run deep and wide, and the inherent risks are the ones that can, and often do, go unrecognized. Threat actors are counting on it; you should also be real with your selection.
IT assessors in an OT environment can lead to issues. Asking the basketball team to assess and audit the football team or baseball team is a compare and contrast situation. They all use balls and play on fields, but the game and rules are all different, not to mention the injuries. There are many independent third parties that have the owner/operator experience and cover from field instrument and control element up and to enterprise.
Safety and environmental is paramount and we need to understand the difference between a secure non-productive system and a secure but productive system. Our nation depends on it.






Comments