February 2014, Vol. 241 No. 2
Features
Benefits Of Network Level Security At RTU Level
New security capabilities at the remote terminal unit (RTU) level are substantially easing implementation of cybersecurity measures in SCADA systems.
Traditionally, technology has been a problem with SCADA security. SCADA technology differs from that in the PC and networking world. RTU platforms are often proprietary and incompatible with PCs. Common SCADA communications protocols are unknowns in the IT world. Those add up to expensive treatment of the SCADA system as an uncommon entity when it comes to cybersecurity.
New technology at the RTU level is making a major difference. New-generation RTUs reside on IP networks and support the same security measures as those that are familiar to the computer and networking world. They allow implementation of common, proven, network-level security measures instead of customized, local-level measures. The result is much quicker and considerably less expensive implementation of cybersecurity measures for SCADA systems.
The most common RTU security features include the following:
Firewall
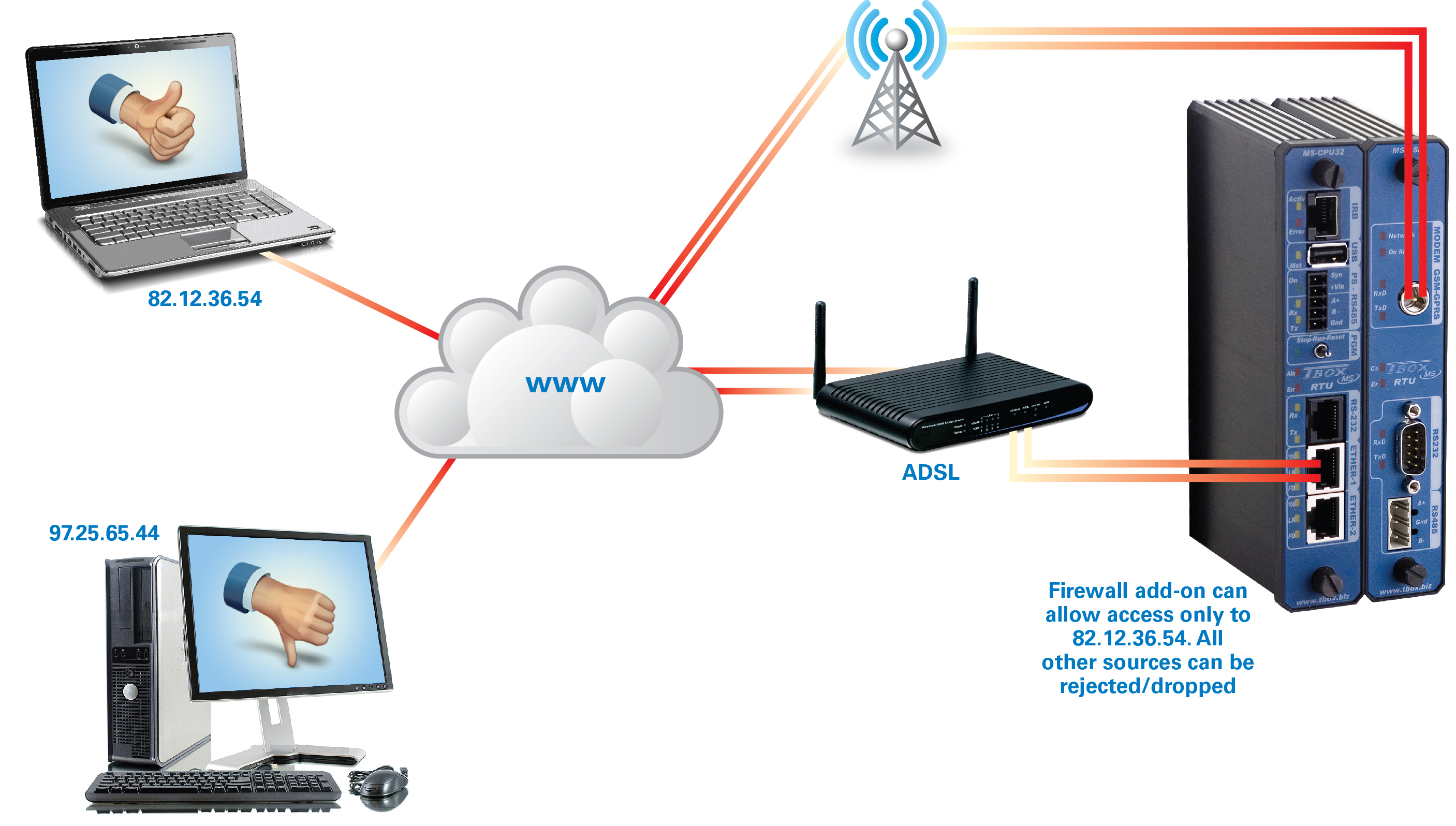
A firewall is a device or software capability designed to allow or deny network transmissions based upon a set of rules. The firewall is used to protect networks from unauthorized access while allowing legitimate communications to pass. A firewall provides a good first line of defense in a secure SCADA system. Using a firewall at each RTU simplifies protection of wireless SCADA networks which cover large, geographical areas that are impossible to secure physically.
The firewall provides access protection for any incoming or outgoing IP connection. Ethernet ports and cellular, such as GPRS or 3G connections, can be protected. Menu interaction allows the user to define one or more rules to allow or deny access. In a simple example, an RTU firewall can allow access-only to a device with a specified IP address. That could be the SCADA host or “master” PC.
Typically, a combination of criteria is specified. An example is “packet filtering” which would be based on port numbers, protocol and the source IP address. This setup provides a defense against an array of threats, including “ping flooding,” denial-of-service and “spoofing.”
Authentication
A major threat to SCADA systems is that third parties can gain remote access to RTUs and operate process equipment such as compressors and pumps. Equipment can be operated in a manner that causes damage, creates safety risks, disrupts the process, increases power use and reduces service life.
Authentication is a reasonable measure to address such threats. It presents little additional loading in terms of network bandwidth and processing power. However, authentication does not provide data security.
If third parties must be prevented from eavesdropping on the network and reading messages, encryption is the solution. Two of the authentication methodologies that have recently been put into practice in the RTU world are IEEE 802.1X and DNP3 Secure Authentication.
IEEE 802.1X
IEEE 802.1X is a standard for passing extensible authentication protocol (EAP) over a wired or wireless local area network (LAN). It provides authentication for devices wishing to access a network. It prevents rogue devices from attaching to the LAN or RTU port. That, in turn, prevents unauthorized access to proprietary information and the ability to download parameters or commands.
DNP3 Secure Authentication
The DNP3 User Group Steering Committee has ratified a security extension that mandates the authentication of master devices through the use of one-way cryptographic hash functions employing a shared key in order to access critical DNP functions. DNP3 Secure Authentication is an extension to the existing DNP3 standard incorporating IEC62351 Version 2.0 authentication on top of the DNP3 communication protocol. According to the DNP3 User Group, the purpose of this specification is to define a protocol mechanism that:
• A DNP3 outstation can use to unambiguously determine that it is communicating with a user who is authorized to access the services of the outstation.
• A DNP3 master can use to unambiguously determine that it is communicating with the correct outstation.
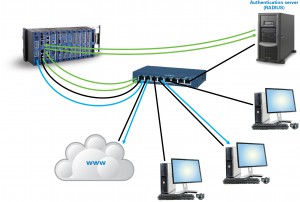
DNP3 Secure Authentication uses a challenge process. When a command to operate a compressor or pump is received from the server (blue arrow in the accompanying diagram), the RTU challenges the server to be sure it is a legitimate node on the network (yellow arrow in the accompanying diagram). The server responds with an authentication message. If the server authenticates correctly, only then will the RTU perform the action (green arrows).
The authentication key is updated at regular intervals in order to prevent old keys from being stolen and reused. If an RTU does not receive a new key within a specified time limit, it will mark the key as stale and ignore commands until a new key is provided.
Encryption
Encryption is the process of encoding messages or information in such a way that eavesdroppers cannot read it but authorized parties can. Unlike authentication, encryption provides data protection. It is also an excellent measure to prevent tampering with messages in order to falsify information or send commands to operate process equipment. If data security is not an issue, SCADA users can opt instead for authentication.
In encryption, a secret key is applied to a message to change its content in a particular way. Both sender and recipient can encrypt and decrypt all messages that use this secret key.
The problem with secret keys comes when they are exchanged over the Internet. Anyone who knows the secret key can decrypt the message. One solution is asymmetric encryption in which there are two related keys – a key pair.
A public key is made freely available while a private key is kept secret. Any message that is encrypted by using the public key can only be decrypted by using the matching, private key.
Processing capability requirements have prevented use of asymmetric encryption in older RTU products but newer models provide more than the necessary performance.

Certificate Authentication
Certificates are used on the Internet as a method of authenticating web sites. When a user visits a secure web site, the web server will send a copy of the certificate to the user’s web browser. This way, the browser is assured that it is visiting the correct web site rather than an imposter or phishing site.
Certificates are also used in encrypted IP networks for authentication at the beginning of a session. This technology is available in SCADA products. A certificate is a package of information that identifies a user or a server and contains information such as:
• Organization name
• Organization that issued the certificate
• Unique identification
• Valid dates
• Digital fingerprint
• The user’s public key
TLS/SSL
Transport layer security (TLS) and its predecessor, secure sockets layer (SSL), are cryptographic protocols that provide communication security over the Internet. TLS/SSL protocols allow client-server applications to communicate across a network in a way that is designed to prevent eavesdropping and tampering.
TLS/SSL encrypts connections at the application layer, for example, FTP, HTTP and SMPT. Secure versions such as FTPS, HTTPS and SMPTS, use the same encryption algorithm.
Virtual Private Network
A virtual private network, or VPN, uses authentication to deny access to unauthorized users and encryption to privately transport data packets over networks that are, otherwise, unsecured. A VPN is a good alternative to firewalls in wireless SCADA networks, which can’t be physically secured and are prone to eavesdropping.
Products such as OpenVPN are feasible for implementation in RTU products. This provides secure communications for industrial protocols such as Modbus/TCP. OpenVPN is an open source software application that creates secure point-to-point connections.
OpenVPN user-space implementation allows portability across operating systems and processor architectures, firewall and NAT-friendly operation, dynamic address support, and multiple protocol support.
OpenVPN uses TLS/SSL for key exchange and allows peers to authenticate each other using a pre-shared secret key, certificates, or username/password. OpenVPN uses the OpenSSL library to provide encryption. All the ciphers available in OpenSSL can be used.
Conclusion
Support of such network-level security measures as authentication, encryption, firewalls, TLS/SSL and virtual private networks in RTU products substantially ease implementation of cybersecurity measures in SCADA systems. Instead of treating the SCADA system as an uncommon entity that requires expensive customized security measures, engineers can apply proven security measures that are popular in the computer and networking world.





Comments