February 2014, Vol. 241 No. 2
Features
What Managers Should Know About Pipeline SCADA Cybersecurity
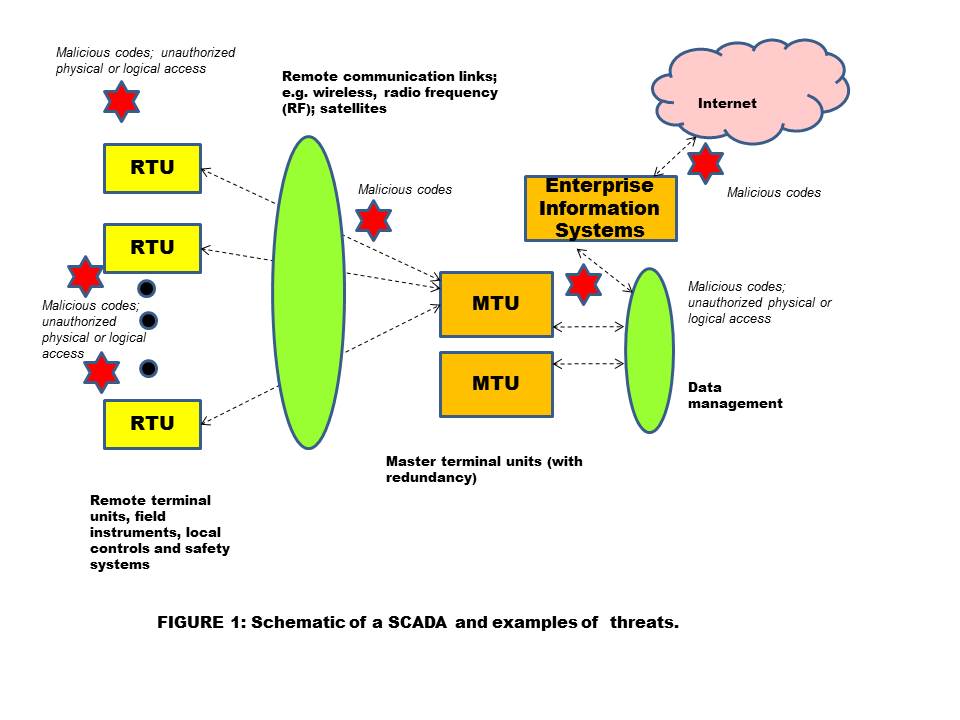
Supervisory control and data acquisition (SCADA) is a pivotal tool in achieving impressive productivity and reliability of pipelines. However, SCADA systems face cyber threats that could render them inoperable, causing substantial adverse effects on profitability. Worse yet, the threats could deactivate some safety systems, and jeopardize safety of the pipeline, workers and neighbors.
This article looks at SCADA cyber threats and possible solutions from the viewpoint of management. The focus is at the managerial level, and details of intricate technical nature, such as SCADA programming, firewall protocols and intrusion detection system protocols are omitted.
Simply put, a manager wants to ensure the SCADA system is capable of dealing with as many threats as possible. The bottom line is overall reliability and safety. Astute managers want to ensure:
• SCADA system will provide effective protection against known threats.
• There is a plan of action that can be implemented to recover from a security breach or security event relatively quickly.
• Employees are trained in procedural systems to ensure safety.
• Sufficient safeguards are in place to ensure security of the safety systems.
• There are periodic system audits.
• Systems are in place to upgrade SCADA systems in an efficient way.
So what are the threats? Threats are the vectors that could affect SCADA. Shown (Figure 1) is schematic of a pipeline SCADA and some examples of threats.
Broadly stated, these dangers could originate either from inadequate security procedures (e.g. access control: poor authentication techniques or poor change management in access rights of an employee along with changes in their positions within the company), or due to equipment shortcomings – hardware or firmware, or software failures (firewalls, intrusion detection programs).
While a large number of threats could be intentional, some can be accidental. In either case, the net result could have adverse effect. In addition, the term vulnerability is used to indicate “holes” or deficiencies in the existing SCADA system that could expose it to cyber threats.
Threats work in numerous ways. Someone can introduce malicious code in the SCADA commands that stops the SCADA, gives erroneous information to SCADA operators or affects safety and integrity. Malicious codes (logic programs that contain executable statements) take various forms, including viruses, Trojan horses, worms and or logic bombs.
These codes can cause “denial of service,” or give deliberately erroneous information (on the HMI screen), which can cause the operator to take erroneous steps. SCADA systems are typically interfaced with a company’s management (enterprise management) systems, as well as with the Internet. Traffic from the Internet can introduce malicious code (“hacking”). Also, workers or contractors may bring in flash drives that insert malicious code into SCADA. Remote access by wireless or Internet can do the same.
In order to protect the SCADA, systems include a number of design and operational concepts, including:
• Defense-in-depth: The idea is that if we provide multiple layers of protection, the possibility that a threat could harm SCADA will be minimized. Firewalls, intrusion detection algorithms, access control, virus control algorithms, encryption (though not common) and network partitioning are some multi-layer of protection methods.
• Authentication and authorization (tight control and management of access rights) systems.
• Periodic audits and testing.
• Network partitioning: This idea is similar to the equipment separation used to ensure chemical safety by localizing the impact of an unsafe event. Network partitioning aims to limits the effect of a security event to that segment or partition of the network. Data traffic is controlled by appropriate fire walls and intrusion detection systems.
Obviously, ensuring cybersecurity is not a one-time undertaking; it is an ongoing process. Consider the following steps:
1. Conduct a gap-analysis or a risk assessment of your system. Typically, a team of subject matter experts may conduct this assessment. Potential threats are evaluated in view of the existing safeguards of the SCADA system. The team may learn how likely a threat is and its potential damage.
2. After the evaluation, a “risk value” can be assigned. Risk value is the combined likelihood and consequence of a security event. For qualitative determination of risk, a risk matrix may be used. Based on a company’s risk averseness (or risk acceptance), risk matrix assigns values and also shows acceptable and unacceptable ranges of risk.
(Although SCADA security problems resemble information technology (IT) system issues, there are significant differences in the objectives of an IT system and a SCADA system. SCADA system security processes should be a joint and cooperative effort between the SCADA engineers and IT personnel.)
3. After risk levels are determined, the question becomes, “Is that risk acceptable? If the answer is “yes,” no further action is necessary. The existing system of safeguards is considered adequate. On the other hand, if risk level is higher than the acceptable level, additional safeguards would be required.
• Consider implementing guidelines and procedures for access control, update of access control with change in employee status and system upgrades (“patch management”).
• Consider best management practices suggested by a number of standards, including ANSI/ISA 99.00.01-2007, NIST 800-82; 800-53, API-1164, IEC-62443 and corporate best policies.
• Implement guidelines for contractor screening, procurement and employee hiring with a focus on potential cybersecurity threats.
• Have systems in place to ensure relatively trouble-free system upgrades (change management).
• Consider developing and implementing a response plan, sometimes called a “disaster recovery” plan.
• Develop a culture of trust and not a “police state” mentality. Security procedures are necessary; however, employee and contractor trust are also important.
As a concluding note, keep in mind that SCADA security is an on-going process which requires resources and discipline. With the escalation of security threats, SCADA security is emerging as a crucial necessity for many installations.
Author: G.C. Shah is a senior advisor in safety, health and environmental issues at Wood Group Mustang in Houston. His certifications include CFSE, CAP, PE and CSP. He has written about 50 papers on process safety, environmental management, process and project engineering, and management. Shah holds a master’s degree in chemical engineering and environmental management, and degrees in computer science and process control. He can be reached at (ghanshyam.shah@mustangeng.com).





Comments