February 2015, Vol. 242, No. 2
Features
Energy Providers, Including Pipelines, Vulnerable To Malware
Financial services firms may have a slight edge in security readiness over their energy sector counterparts, but not by much. These two industries – highly targeted by cybercriminals – must move quickly to address their cybersecurity deficiencies and shore up their defenses against advanced malware threats.
Combating the malware behind headline-grabbing data breaches is a constant struggle for organizations of all sizes. Cybersecurity professionals are facing a new, harsher reality of increasingly sophisticated threats that make defending against data breaches a much more daunting task. In response, security teams are scrambling to implement new strategies and deploy emerging cyber-defense technologies.
Not all industries, however, face the same cybersecurity challenges in today’s shifting threat landscape. While the prime target for cybercrime is the financial services industry, the energy industry – including pipeline and gas companies – face significant risks as well. Vulnerabilities in both industries have been recognized as critical and vulnerable components of our national infrastructure by the president and the Department of Homeland Security.
ThreatTrack Security conducted a study to uncover how cybersecurity professionals within these two critical industries are dealing with today’s cyber threats. Through a third-party research firm, ThreatTrack Security surveyed 200 IT security professionals (100 respondents from each sector) on a wide array of cybersecurity issues.

The study revealed that many respondents are fully aware of their new cyber reality, with nearly 40% saying it was either a certainty or highly likely that their organization would be the target of an advanced persistent threat (APT) or targeted attack within the next 12 months.
While it is definitely a positive development that so many security professionals are preparing themselves for a wave of advanced malware attacks, their ability to effectively combat these threats is questionable. The survey found that 35% of respondents reported endpoints on their network had been infected by malware that evaded their defenses during the last 12 months. Moreover, 58% of respondents cited the complexity of malware as the most difficult aspect of defending their organization.
How are organizations responding? The study found that they are focusing on training their IT staff on new technology and cybersecurity strategies (50%); implementing new policies (35%); and investing in advanced malware detection technology (34%).

Malware: A Plague On Both Houses
While the financial services industry and energy companies face different cybersecurity challenges, their ongoing struggle with malware is remarkably similar.
Asked whether any of their endpoints had been infected by malware that evaded detection by their traditional signature-based defenses such as antivirus, email security or firewalls in the last 12 months, 35% of respondents overall said their endpoints had been infected at least once.
Respondents within the energy sector (37%) reported a 6% higher rate of infection than their financial services counterparts.
And 78% of companies with security budgets between $750,000 and $1 million reported infections, but that number decreased dramatically to 35% when security budgets exceeded $1 million – demonstrating that organizations with the right resources and making the right investments can significantly improve their security postures.
About 50% of respondents overall said email was the top threat vector through which their organization encounters the most malware. Web was cited by 34% of respondents as their top threat vector.
Breaking it down by industry, 61% of respondents at energy companies said email is their biggest threat vector; 42% of respondents at financial services companies said it was the web, but email was a close second with 39%.
Email was most often cited as the top threat vector by organizations with more than 500 employees (54%), as well as firms with security budgets of less than $500,000. Web was most often cited as the top threat vector by organizations with 250-500 employees (60%), as well as by firms with security budgets exceeding $1 million (37%).
Surprisingly, only 3% of respondents cited mobile as their top threat vector – despite continued hype around BYOD and the rise of malware targeting mobile devices. PC-based malware is still the dominant threat that organizations face.
Hacktivists Vs. Cybercriminals
To further illustrate the differences between the threats each sector faces, the study asked what type of threat actor respondents felt were most likely to launch a cyberattack against their organization.
While 34% of security professionals in the energy sector cited hacktivists, only 25% of respondents in financial services agreed. And 36% of respondents in the financial services field identified organized cybercrime syndicates as the threat actor type that most concerned them. Only 15% of energy security professionals agreed. Moreover, 12% of energy companies fear attacks from foreign governments, while only 7% of financial services firms do.
Other responses were: insider threats from current or former employees (7%, energy; 9%, financial services), terrorists (9%, energy; 5%, financial services), foreign competitors (8%, energy; 0%, financial services), domestic competitors (2%, energy; 5% financial services), and the U.S. government (4%, energy; 3% financial services).
Both sectors were consistent in what they view as their top security challenges.
Asked to identify the most difficult aspects of defending their company from advanced malware, 58% of respondents answered complexity of malware. The next most difficult problem at 37% is the high volume of malware attacks, said respondents from both sectors.
One-quarter of the respondents cited ineffectiveness of anti-malware solutions. More than one-fifth of respondents (22%) attributed their malware problems to lacking enough highly skilled security personnel, such as malware analysts.
Moreover, about 16% of respondents in both sectors cited over-reliance on industry compliance standards or government regulations as a guide for organizational security strategy.
Data Breach Disclosure Lacking
Asked whether their company had ever investigated or addressed a data breach that it did not disclose to customers, partners or stakeholders, a sizeable percentage (17%) in the energy sector answered “yes.” Despite working in an industry governed by some of the most mature and stringent security regulations, 11% of respondents in the financial services arena admitted to investigating breaches that were never disclosed.
The highest rate of non-disclosures (44%) came from companies with security budgets of between $750,000 and $1 million.
Conversely, most respondents (87%) within enterprises in both sectors with security budgets of more than $1 million responded that they were unaware of any data breaches that were not disclosed – perhaps reflecting strict compliance with regulations and more mature corporate governance practices at larger organizations.
These results are welcome findings and are dramatically different from a ThreatTrack Security October 2013 survey of enterprise malware analysts, 57% of whom said they knew of data breaches their company did not disclose.

Resignation Or Accepting Reality?
The study found that a significant portion of security professionals in the financial services and energy sectors believe their networks will be targeted by sophisticated cybercrime in the next 12 months.
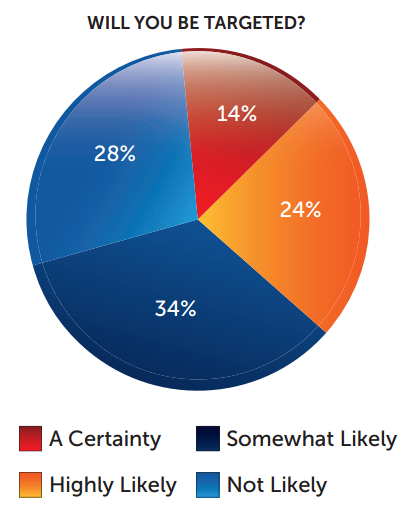
As a result, 38% of all respondents said it is either a certainty or highly likely that in the next 12 months their company will be the target of an Advanced Persistent Threat (APT), targeted malware attack or other sophisticated cybercrime or cyber-espionage tactic. Another 35% said it was somewhat likely.
A higher percentage of energy companies (44%) than financial services firms (31%) expect to be hit by one of the above attacks. The highest percentage of companies (23%) that believe an attack is a certainty were those with a security budget exceeding $1 million, implying that larger organizations are more aware of their cybersecurity situation than smaller organizations and may even be actively combating these threats on a regular basis.
It is certainly a positive development that so many security professionals within energy and financial services enterprises recognize they are targets. This shouldn’t be viewed as security professionals throwing in the towel, but rather accepting today’s cyber reality and adjusting tactics in response. The study also demonstrated that security professionals in both sectors are planning to improve their security posture.
Planning New Defense
Asked what their organization plans to do this year to strengthen its cybersecurity, half of the respondents said their companies would train existing IT staff on new technology and cybersecurity strategies.
In past ThreatTrack Security research, training has often been cited as a top priority, but it was generally related to user training to increase awareness of potential security risks. This study revealed that security professionals within finance and energy organizations feel it is an imperative to re-educate IT staff on new security strategies and emerging advanced threat detection technologies. This implies recognition that the old network security model is dated. Staff and technology need to evolve together to combat today’s advanced malware.
Now, 35% of respondents said their companies would implement new policies, such as limiting network access privileges and educating all employees about cybersecurity. For another 34%, investing in advanced malware detection technology was a top priority.
In addition to hiring specially trained cybersecurity staff (19%, energy; 16% financial services), respondents reported they are looking for outside help to solve their security challenges.

Nearly 20% of security professionals within financial services organizations said they had plans to contract with a Managed Security Services Provider (MSSP) or systems integrator for outsourced security support and/or incident response. A smaller percentage – just over 10% of security professionals within the energy sector – reported the same.
Conclusion
As concern about data breaches continues to grow, U.S. energy and financial services companies remain vulnerable to the advanced malware threats used by cybercriminals to evade defenses and steal data, including customer information, intellectual property and more. Consequently, the U.S. economy and its critical infrastructure also remain vulnerable to cybercrime.
Financial services firms may have a slight edge in their readiness over their energy counterparts, but not by much. These two highly targeted industries must move quickly to address their cybersecurity deficiencies. Fortunately, many security professionals within each sector seem to grasp the challenges they face and recognize that they will be targeted by advanced malware threats. They have plans to improve their security readiness, but must act quickly to shore up their defenses.
Author: Stuart Itkin leads ThreatTrack’s global marketing strategy and operations and has over 20 years of executive experience creating and executing marketing and product strategies at a variety of technology and software companies. Previously, he led global marketing at companies including CEB, Kronos, Zebra Technologies, Lucid and Symbol Technologies.





Comments