February 2015, Vol. 242, No. 2
Features
Improving Cybersecurity Defenses In Oil And Gas Applications
In recent years, there have been a number of high-profile, advanced malware threats that targeted or attacked the energy sector such as Dragonfly, Stuxnet, Flame and Shamoon. And while these threats need to be taken into account when analyzing and preparing for potential security risks, they actually only account for a low number of overall threat sources.
Industry research shows that internal – not external – sources make up more than 60% of all cybersecurity threats.
Oil and gas networks, in particular, can be more susceptible to internal incidents because many devices on the network run 24 hours a day, seven days a week, and often lack the security updates and antivirus tools needed to protect against vulnerabilities. In addition, “wide open” network layouts and a lack of isolation between subsystems make it easy for problems to spread quickly throughout the network.
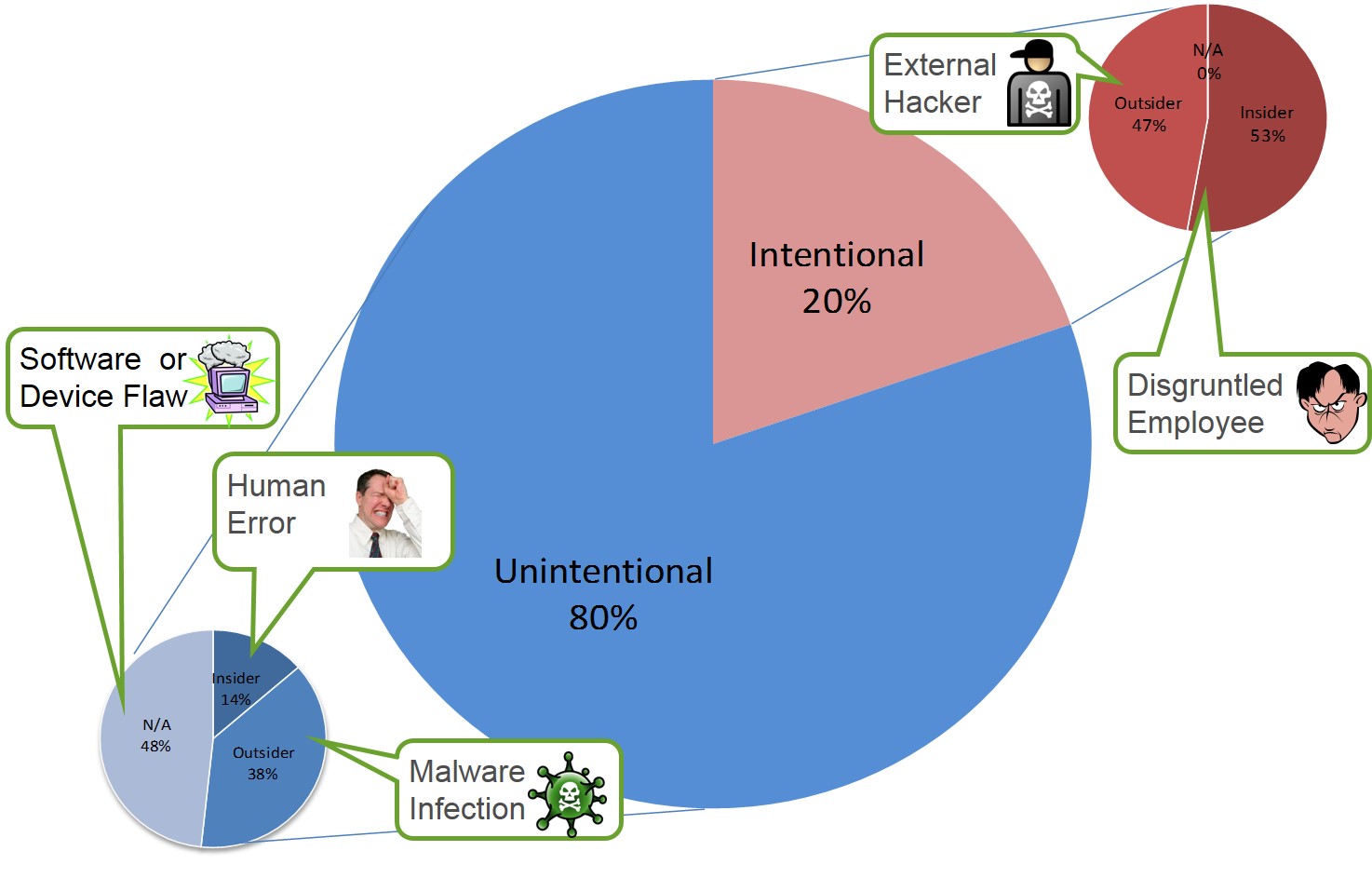
Most cybersecurity threats and incidents are unintentional and occur inside industrial networks.
Source: The Repository of Industrial Security Incidents, 2011.
A firewall protecting the edge of a network can defend applications against many external cybersecurity threats or attacks. However, with more threats originating from inside the network – whether via a USB keys, maintenance systems or visitor laptops – additional security measures need to be taken in order to harden control networks.
To protect oil and gas operations, engineers and network designers must identify new cybersecurity measures.
Solutions Industrial Networks
Information technology professionals have been successfully dealing with cybersecurity threats for years. However, IT teams are concerned mostly with privacy and protecting data, while industrial control systems (ICS) security measures focus on the concern for safety and protecting overall operations. With a focus on privacy and data protection, the solutions applied by IT don’t work for industrial control networks.
Here are a few additional reasons IT solutions won’t work for oil and gas operations:
• Critical, industrial networks can’t be shut down for testing, configuration and maintenance, as is done with business networks. Instead, industrial security products must be set up and maintained while the network is running.
• Industrial networks use unique communication protocols not seen in the IT world and not addressed by IT security products.
• Patching or updating programmable logic controllers (PLCs) is usually not practical.
• Control devices cannot be secured with automated third-party tools.
• Oil and gas applications require hardened equipment that can survive harsh electrical and environmental conditions.
• Industrial networking equipment needs to work for decades, whereas IT gear has a life cycle measured in years.
Finally, engineering staffs need cybersecurity solutions that are simple to use. While they are experts in making products or programming PLCs, they are likely not cybersecurity experts. Thus, industrial security solutions need to be easy to use in order to minimize human error in set-up and ongoing use.
Layered Security Approach
The best approach is to implement a defense in depth strategy in which multiple layers of security are in place and working together to harden the network and prevent incidents.
A key best practice is to implement the zone and conduits model as defined in the ISA IEC 62443 standard. This model provides a framework for network segmentation that prevents cybersecurity incidents from spreading.
“Zones” are logical or physical assets that share common security requirements. The zones then communicate exclusively through secure “conduits.” A conduit is any pathway of communication that enters or exits a security zone.
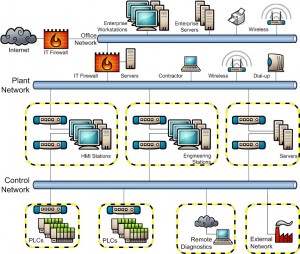
Figure 1: Implementing zones and conduits enable a layered approach to network security.
To apply a zones and conduits concept, first, you need to define the security zones. In the network diagram (Figure 1), there are groups of PCs that act as human machine interface (HMI) stations, engineering workstations and servers – each of these fall into their own security zones. In addition, the two groups of PLCs and two remote network connections make ideal security zones.
The next task is to locate the conduits of communication in the network. Conduits are the perfect place for implementing security measures such as industrial firewalls to ensure that only the necessary traffic is allowed to pass. These security measures compensate for the fact that the devices they protect have insufficient built-in security measures. This approach is cost-effective because it doesn’t require upgrades to every device or computer in a zone to meet security requirements.
Cybersecurity For Pipelines
The primary goal of a cybersecurity strategy is to improve safety, reduce network downtime and improve overall productivity.
When issues arise it can be costly. Here’s a real-world example of how cybersecurity incidents can inadvertently happen. The controls for an existing oil pipeline were being made. In this situation, it’s an industry best practice to always test and verify in the engineering lab before deploying new code into the field. This time, however, the software was accidentally uploaded to a PLC on the plant network instead of the test network. The oil pipeline was shut down for nearly six hours. Fortunately, no spills or accidents occurred, but the downtime alone cost the company well over $250,000.
To really understand how to improve defenses, here’s a look at how the zone and conduit model can be used to protect pipeline infrastructure.
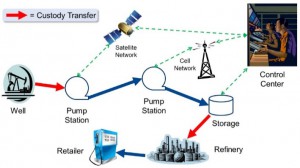
Figure 2: A simplified diagram of a pipeline system showing custody transfer points.
A pipeline system includes the pipeline itself, pump stations and connections to one or more wide area networks (WANs). There are usually several points in the system where custody transfer of the resource occurs with the resource being measured by flow meters. In this case, there are two approaches for defending against cyberattacks.
The first approach is to focus on securing only the critical assets. For example, in the pump station network (Figure 2), the zone that protects critical assets, including PLCs, sensors, pumps and actuators, is the priority zone within the network. Other zones that may group together physical security elements, such as cameras and alarms, are a secondary concern when the main goal is to keep the network up and running and the pipeline operational.
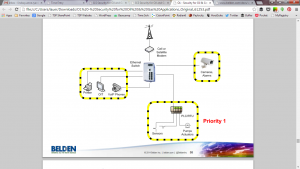
Figure 3: Prioritize the zone that protects the mission-critical assets that keep the network running.
The second approach is to take into account that flow meters connect to two networks for custody transfer – the seller’s PLC and the buyers’ PLC – the latter being an untrusted network. In this situation, the best solution is to insert the flow meter into a demilitarized zone (DMZ) and separate all zones with a multiport firewall. A DMZ is a zone created to allow dual access to a shared resource, but with no direct access – this protects the networks of the buyer and seller.
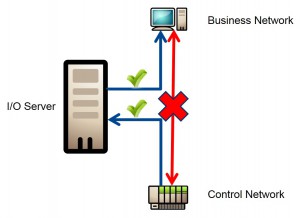
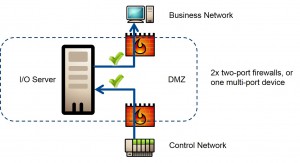
Figure 4: A demilitarized zone, right, allows dual access to a shared resource, without enabling direct access for additional network protection.
Establishing Defense Methods
The best method for securing oil and gas applications against cybersecurity threats is to establish multiple layers of defense that not only work together to prevent network incidents, but also work to contain them, should an incident occur.
Relying on single-layer defensive solutions exposes a network to a single point of failure. Abiding by a defense in depth approach, in conjunction with a comprehensive risk assessment and the ISA IEC 62443 zone and conduit guidelines, will help build strong defenses throughout a pipeline’s network.
Ultimately, industrial cybersecurity doesn’t have to be hard. With the right approach and defenses, oil and gas operations will be able to protect their networks and establish robust cybersecurity solutions.
For more information, view this presentation with tips and advice about improving cybersecurity defenses in oil and gas operations: http://info.belden.com/cyber-security-oil-gas-bc-lp.
Authors: Scott Howard is a commercial engineer for Belden Tofino Security, which he joined in 2007. He has nearly 30 years of experience in embedded system development and has worked with organizations worldwide to help them improve the reliability of control systems through enhanced cybersecurity.
Tim Wallaert is director of Oil & Gas Solutions for Belden, where he leads the company’s expansion into oil and gas, as well as power utility markets. He has spent more than 20 years in industrial automation, helping improve production operation across a range of industries. His current focus is on energy communications and automation as one of the key enablers of the digital oilfield. He holds a bachelor’s degree in electrical engineering from Michigan State University and master’s degree from Case Western Reserve University.





Comments